BestCrypt Corporate 1.12
 BestCrypt Corporate provides protection of data in corporate networks using strong encryption algorithms.
BestCrypt Corporate provides protection of data in corporate networks using strong encryption algorithms.
|
BestCrypt Corporate provides protection of data in corporate networks using strong encryption algorithms.
BestCrypt Corporate includes standard BestCrypt software that performs encryption/decryption operations creating virtual drives acting as regular drives.
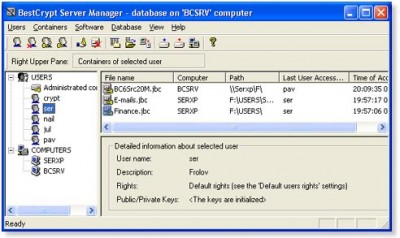
The core of BestCrypt Corporate is BestCrypt Central Manager that provides all range of functions: automatic installation/uninstallation and update of BestCrypt on remote client computers, creation of central Administrating Database on the server.
Central Administrating Database keeps tracks of all passwords used by client computers to create containers to keep data inside in encrypted form.
Secret data kept on client computers can be always accessed by Administrator, even if employee is away or gone.
Central Administrating Database can be also scheduled for automatic backup. BestCrypt Corporate is important tool to keep corporate networks secure and at the same time, it provides easy yet powerful way to manage secret data in networks consisting from 5 to 100 000 computers.
The BestCrypt software performs encryption using the strongest algorithms available including:
BestCrypt Corporate features
Requirements
tags![]() bestcrypt corporate swap file bestcrypt software block chaining chaining mode you can the algorithm can now cipher block hidden containers the swap client computers administrating database
bestcrypt corporate swap file bestcrypt software block chaining chaining mode you can the algorithm can now cipher block hidden containers the swap client computers administrating database
Download BestCrypt Corporate 1.12
![]() Download BestCrypt Corporate 1.12
Download BestCrypt Corporate 1.12
Purchase: ![]() Buy BestCrypt Corporate 1.12
Buy BestCrypt Corporate 1.12
Authors software
 BestCrypt 8.04 beta
BestCrypt 8.04 beta
Jetico, Inc.
BestCrypt software will create and will support encrypted virtual disks.
 BestCrypt Corporate 1.12
BestCrypt Corporate 1.12
Jetico, Inc.
BestCrypt Corporate provides protection of data in corporate networks using strong encryption algorithms.
 BCWipe 7.50.2
BCWipe 7.50.2
Jetico, Inc.
BCWipe ensures that another person will not restore files you have deleted from a disk.
Similar software
 BestCrypt Corporate 1.12
BestCrypt Corporate 1.12
Jetico, Inc.
BestCrypt Corporate provides protection of data in corporate networks using strong encryption algorithms.
 BestCrypt 8.04 beta
BestCrypt 8.04 beta
Jetico, Inc.
BestCrypt software will create and will support encrypted virtual disks.
 BestCrypt Key 7.9
BestCrypt Key 7.9
Passware
BestCrypt Key will recover passwords for virtual hard disks encrypted with BestCrypt (.
 BestCrypt Volume Encryption 5.12.3
BestCrypt Volume Encryption 5.12.3
Jetico Inc.
BestCrypt Volume Encryption software will provide transparent encrypting all the data stored on removable and fixed disk devices.
 CryptoExpert 2007 Professional 7.1.1
CryptoExpert 2007 Professional 7.1.1
SecureAction Research LLC
CryptoExpert is a software which will make transparent encryption using virtual hard drives.
 PrimaSoft Encryption - Service Edition 1.0
PrimaSoft Encryption - Service Edition 1.0
PrimaSoft PC Inc
PrimaSoft Encryption is a Windows program which allows you quickly and easely to run scheduled encryption and decryption sessions as a service process using the latest industry standard strong encryption algorithms: AES (US Advanced Encryption Standard, secret-key encryption also known as Rijndael); Twofish (secret-key encryption); RSA (public-key encryption)
Features:
· Encryption software: service process: You can run scheduled auto-recurring encryption and decryption sessions as a service process.
 CryptoForge 5.5.0
CryptoForge 5.5.0
Ranquel Technologies
CryptoForge is a suite of encryption tools for personal and professional security.
 Secured Drive 1.2
Secured Drive 1.2
Tiasoft, LLC.
Tiasoft Secured Drive is an easy-to-use encryption application that lets you create encrypted logical drive to keep your private and confidential data secure on personal computers, notebooks, and removable media.
 CryptoExpert Express 2.1
CryptoExpert Express 2.1
SecureAction Research, LLC
CryptoExpert Express is an application that encrypt important files
CryptoExpert Express is easy to use on the fly encryption software with user friendly interface.
 P-Encrypt Secure Drive 1.2.2.3
P-Encrypt Secure Drive 1.2.2.3
CadabraSoftware
P-Encrypt Secure Drive (PESD) is a program that can create virtual encrypted disk drives.
Other software in this category
 Paragon Encrypted Disk 3.02
Paragon Encrypted Disk 3.02
Paragon Technologie GmbH
Paragon Encrypted Disk - protect private and sensitive data from potential unauthorized access.
 Info-Lock Home Edition 1.1
Info-Lock Home Edition 1.1
Info-Lock
Info-Lock Home Edition offers you the perfect solution for securely locking your home desktop computer files from prying eyes.
 Adhaero Transit 1.010
Adhaero Transit 1.010
Adhaero Technologies
Adhaero Transit is a tool that enables safe e-business.
 Chameleon 2.0
Chameleon 2.0
Globe Masters Software
 Encode It 2.01
Encode It 2.01
Skylark Utilities
Encode It will allow users to safely decrypt, encrypt or shred one or more files, including complete folders and all it`s sub folders in one easy step.