RegFreeze 5.6
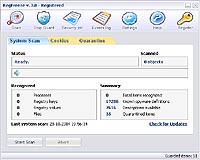
 RegFreeze is a useful application which has as a primary goal the prohibition of many critical data changes without your demand, such as your browser's start page and so forth.
RegFreeze is a useful application which has as a primary goal the prohibition of many critical data changes without your demand, such as your browser's start page and so forth.
|
RegFreeze is a useful application which has as a primary goal the prohibition of many critical data changes without your demand, such as your browser's start page and so forth.
RegFreeze reacts to malicious changes immediately, forbids them and then informs you (or if an automatic mode is enabled, work with such changes automatically).
The specified principle of protection is simple enough, but it is allows to guard your computer from annoying spyware-modules with a maximum degree of reliability. Furthermore, RegFreeze guards Internet Explorer favorites and the most of system files (e.g.: system.ini, win.ini, autoexec.bat) from undesirable changes causing by spyware.
Moreover, RegFreeze contains frequently updated spyware-scanner module, intended for scanning and removals spyware which has already intruded onto your computer.
Start using RegFreeze today and solve all these problems once and for all! Most spyware changes your browser's start page or search page. RegFreeze is intended to prevent the destructive consequences of spyware.
RegFreeze's primary objective is to prevent any important preferences (such as your browser's start page etc.) from being changed without your knowledge. RegFreeze detects changes in a timely manner and notifies you about them (or, if an automatic mode is enabled, processes changes automatically).
RegFreeze spyware scanner will clean your system quickly and effectively! Use RegFreeze and you will forget about spyware forever!
Spyware is a generic term describing any software that secretly installs onto a computer or local network. It sneaks in the background without your permission and performs illegal activities that can cause damage to your PC. Usually Spyware monitors your PC and delivers the information to third parties.
Once installed, Spyware software can do almost everything. Your personal information like e-mail addresses and credit cards can be monitored, snatched up and delivered to third parties without your knowledge.
Spyware is evolving into a monster that might soon become more vicious than e-mail spam and virus attacks combined. Spyware is a technological problem and users need a strong defense to combat it. Let's observe how Spyware can harm your PC.
RegFreeze features
Memory
Processes
Registry entries
Files
Folders
Adware
Spyware
Malware
Unwanted toolbars
Browser hijackers
Unwanted cookies
Browser start page
Browser search page
Autorun entries
Prevents BHO installing
Much more...
>55, known spyware definitions
Known spyware descriptions database
Updated weekly
Lifetime free database updates for registered users
Quarantine capabilities
User-friendly interface
Fastest work
24-hour customer support
Lifetime free updates of RegFreeze
Registered users are eligible for priority technical support
Limitations
tags![]() without your start page your browser known spyware third parties lifetime free customer support your knowledge registered users spyware scanner automatic mode changes automatically your computer
without your start page your browser known spyware third parties lifetime free customer support your knowledge registered users spyware scanner automatic mode changes automatically your computer
Download RegFreeze 5.6
Purchase: ![]() Buy RegFreeze 5.6
Buy RegFreeze 5.6
Authors software
 RegFreeze 5.6
RegFreeze 5.6
ActualResearch Inc
RegFreeze is a useful application which has as a primary goal the prohibition of many critical data changes without your demand, such as your browser's start page and so forth.
Similar software
 RegFreeze 5.6
RegFreeze 5.6
ActualResearch Inc
RegFreeze is a useful application which has as a primary goal the prohibition of many critical data changes without your demand, such as your browser's start page and so forth.
 Max Anti Spyware Pro 15.8
Max Anti Spyware Pro 15.8
Max Secure Software
Max Anti Spyware is the only product in the market today which not only scans and removes Spyware but also blocks them from installing on your PC.
 Spyware Scanner 3.0.18
Spyware Scanner 3.0.18
East Soft Inc
Spyware Scanner utilizes a sophisticated database of malware infections to detect and remove malware from your computer.
 Spyware Scrapper 3.2
Spyware Scrapper 3.2
SpywareScrapper.com
These days spyware, adware and other malicious software programs are everywhere, and it seems almost impossible to stop them.
 AAA Spyware C.O.P. 10.0
AAA Spyware C.O.P. 10.0
Spyware C.O.P.
This product will scan your P.
 ZeroSpyware 3.4
ZeroSpyware 3.4
FBM Software
ZeroSpyware is the only anti-spyware application which removes all spyware and leaves nothing behind.
 The Spyware Detective 1.4
The Spyware Detective 1.4
Fastlink2
The Spyware Detective finds adware and spyware in the system using an comprehensive database of definitions.
 Spyware Medic 1 build 624
Spyware Medic 1 build 624
WinMedic Software
Spyware Medic is a spyware remover tool that will protect the privacy of your personal information by removing Spyware, Adware, Key Loggers, Browser Hijackers, Malware and other dangerous programs that hide on your system and spy on you without your knowledge.
 1-ACT Spyware Remover 2006 1.0
1-ACT Spyware Remover 2006 1.0
Only PCTools
1-ACT Spyware Remover 2006 is a useful spyware removal tool with a security technology that protects your PC from thousands of potential aggressive spyware, trojans, adware, keyloggers, racking components, spybots, malicious content and other potentially unwanted software.
 Spyware X-terminator 5.0.3.3
Spyware X-terminator 5.0.3.3
StompSoft
Spyware X-terminator is a useful program that can effectively remove spyware and adware and can restore your systems performance.
Other software in this category
 Registry Watch 3.0.03
Registry Watch 3.0.03
Easy Desk Software
Registry Watch takes a snapshot of the Windows Registry and then you can review any changes made in the Registry at a later time.
 Registry Analyst 1.2
Registry Analyst 1.2
Yavsoft
Does your computer work low? Does your system crashes often?
The reason of these problems could be in is the system registry.
 Work With Registry 3.3
Work With Registry 3.3
Useful Utils
Work With Registry is an utility for cleaning invalid parameters from the Registry.
 RegRepair 2000 4.0.04
RegRepair 2000 4.0.04
EasyDesk Software
The only Windows Registry utility that repairs IOS error conflicts and more.
 Resplendent Registrar Registry Manager 5.02
Resplendent Registrar Registry Manager 5.02
Resplendence Sp.
Registrar Registry Manager offers a very complete and safe solution to administrators and power users for maintaining the registry on both their desktops and remote computers on their network.