Permission Analyzer 2.3.0
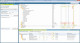 With Permission Analyzer, you will be able to determine whether your system access permissions are appropriately set, need to be changed or have been altered.
With Permission Analyzer, you will be able to determine whether your system access permissions are appropriately set, need to be changed or have been altered.
|
With Permission Analyzer, you will be able to determine whether your system access permissions are appropriately set, need to be changed or have been altered. As a network administrator or a division manager it is hard to gain an overview of the access rights within a computer network.
In general, it is not possible to check the number of access rights per user or user group. If a freelancer is accidentally placed in a user group that has access to, for example, quotes, then it can be harmful to the company.
Permission Analyzer gives you a clear overview of the access rights of each user or user group. You are then able to continually supervise the access rights of the computer network within the organisation.
Apart from the overview of access rights, Permission Analyzer can also give you an overview of the software installed on each workstation. The program gives an answer to questions such as:
tags![]() access rights user group the access permission analyzer which users computer network
access rights user group the access permission analyzer which users computer network
Download Permission Analyzer 2.3.0
![]() Download Permission Analyzer 2.3.0
Download Permission Analyzer 2.3.0
Purchase: ![]() Buy Permission Analyzer 2.3.0
Buy Permission Analyzer 2.3.0
Authors software
 Permission Analyzer 2.3.0
Permission Analyzer 2.3.0
Perdemia
With Permission Analyzer, you will be able to determine whether your system access permissions are appropriately set, need to be changed or have been altered.
Similar software
 Permission Analyzer 2.3.0
Permission Analyzer 2.3.0
Perdemia
With Permission Analyzer, you will be able to determine whether your system access permissions are appropriately set, need to be changed or have been altered.
 EMCO Permissions Audit 1.0
EMCO Permissions Audit 1.0
EMCO
EMCO Permissions Audit can help to find security holes by reporting on specific access rights a user has within a Domain to folders mapped via a share.
 Exchange Permission Manager 2.0
Exchange Permission Manager 2.0
MRH Technology
Exchange Permission Manager (EPM) is an application that provides the ultimate point of access for setting Exchange Information Permissions and for maintaining your sanity as an Exchange administrator.
 Web Research Network Add-on 2.5
Web Research Network Add-on 2.5
Macropool
The Web Research Network Add-on creates network collections that can be used easily by multiple users on a local area network and over the Internet.
 Encrypted RunAs 1.1.6
Encrypted RunAs 1.1.6
Wingnut Software
Encrypted RunAs is a small tool that is created to make the job of Administrators a little easier, it can be used to run applications or software installations with access rights a standard user does not have.
 Access Boss 3.2
Access Boss 3.2
FSPro Labs
Most important among them are security issues and control over PC usage by individuals.
 ProjectTrack Collaborative Edition 2007.1.8 - Build 658
ProjectTrack Collaborative Edition 2007.1.8 - Build 658
iLore
The collaborative edition of ProjectTrack is targeted to companies where several people need to manage projects in a multi user environment.
 indexsoft Access Manager 2.12
indexsoft Access Manager 2.12
IndexSoft
The powerful web based manager of .
 FileSpy 3.0
FileSpy 3.0
SkySof Software Inc.
FileSpy allows users connected to a network with Novell Netware to see all the users who are using a specific file.
 Protector2 2.4
Protector2 2.4
Jan Dolinay
Protector2 is a tool created to increase security on computers running on Windows 9x.
Other software in this category
 EMCO Network Inventory 5.0
EMCO Network Inventory 5.0
Emco Software
EMCO Network Inventory is a useful and powerful utility for hardware and software inventory and audits on networks.
 NetworkView 3.62
NetworkView 3.62
NetworkView Software
NetworkViewGet is a useful tool with the help of which you can get a full graphical map of your network!
NetworkView is a compact network discovery and management tool for the Win32 platform : in a few minutes, it will discover all TCP/IP nodes and draw a full graphical map (including routes) using DNS, MAC addresses, SNMP WMI, NetBIOS and TCP Ports information.
 Network Inventory Manager 3.0.11.5
Network Inventory Manager 3.0.11.5
Microforge.net Limited
Network Inventory Manager is a tool that helps network administrators and help desk staff to more easily manage their networks.
 AppSpy 2.2
AppSpy 2.2
SkySof Software Inc.
With AppSpy managers can easily track the usage of particular files and applications on a Novell Netware File Server within their company.
 DirSpy 2.8
DirSpy 2.8
SkySof Software Inc.
DirSpy allows you to see all those using network files within a specific directory.